Security automation for modern software
BestDefense gives engineering, security, and infrastructure teams instant clarity on what’s exploitable, what will break under load, and exactly how to fix it—automatically.
.png)
.png)

.png)
.png)
.png)
.png)
.png)


.png)
.png)

.png)
.png)
.png)
.png)
.png)


Today's software security solutions are slow to deploy, overpriced, and leave you exposed.
.png)
The result? High costs, delayed fixes, and the constant feeling that your team is always one step behind.
Cyber Attacks are not slowing down.
Why should you?
435million
Online accounts breached in Q1 2024 alone
3,205
Data compro-mises reported in 2023
15.4million
DDos attacks annually
We make cybersecurity simple
Our AI finds what is broken. And fixes it for you.
Identify Security Risks
We run automated penetration tests to uncover vulnerabilities attackers could exploit.
AI Code Remediation
Fix vulnerabilities with a few clicks—so your team can act quickly and stay aligned with industry standards.
Simulate real-world attacks
Reconnaissance & planning like a hacker would.
Identify vulnerabilities
Continuous penetration testing with live exploit data.
Report & analyze
Clear, actionable findings aligned to business risk.
Track & fix with AI
Automated remediation guidance and code fixes.
Set up and Deploy in Minutes. Not days.
What Do our Customers Say?
"BestDefense.io helped us find critical vulnerabilities and helped to drastically reduce the amount of time to resolve them through their automated workflows. This allowed us to secure enterprise customers who required we had a 3rd party audit."
— Thariq Kara (BiteData.io)
"BestDefense.io helped us validate our blockchain under real-world stress and accelerated our SOC 2 compliance. A true top-tier cybersecurity partner"
— RJ Randall (NCOG)
"After implementing BestDefense, we cut our vulnerability detection time by 60% while keeping our deployments on track. I'm finally able to focus on strategic security initiatives instead of constant firefighting."
— Glen Jacinto (Hyacinth BPO)

Our Confidence Framework
Proactive Security
Automated vulnerability testing and continuous threat detection.
Resilient Performance
Identify weaknesses early to prevent downtime, latency, and customer impact before they happen.
Built‑in Compliance
Stay audit-ready with automated mapping to SOC 2, ISO 27001, HIPAA, PCI-DSS, and GDPR.
DevOps Integration
Detect vulnerabilities and compliance gaps before deployment for faster, safer releases.
Continuous Improvement
Real-time analytics drive stronger performance, tighter security, and continuous optimization across your environment.
OUR APPROACH
Integrate. Automate. Secure.
Vortex : Automated Penetration Testing
Proactively discover and fix vulnerabilities — automatically mapped to compliance frameworks and turned into dev tickets so you never fall behind
LEarn More

Maelstrom:
The Ultimate Cloud Resilience
Simulate real traffic demand to ensure your platform performs flawlessly at any scale.
LEarn More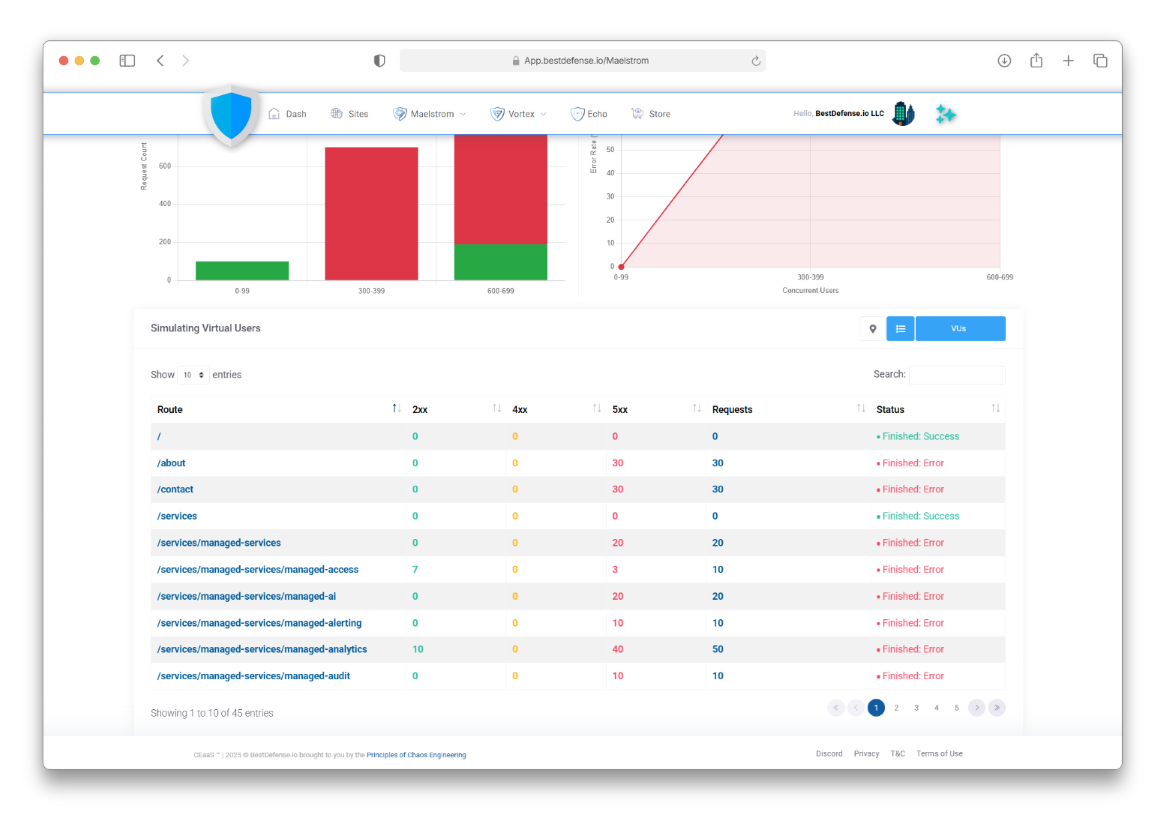

.png)
.png)
.png)
.png)
.png)
Compliance is a Click away.
BestDefense.io Will also help you prepare for compliance
Need Fractional CISO support?
BestDefence offers Fractional Ciso solutions to ensure you meet you security needs.
Looking for Cyber Insurance?
BestDefense can set you up with the best Cyber Insurance on the market.
Do you need compliance training?
BestDefense will ensure you and your staff are trained for compliance or to ensure your risk of human engineering is diminished.
From reactive to proactive, from technical to strategic
BestDefense transforms how you approach cybersecurity
Before
Overwhelmed by Alerts
Explaining technical details
Reacting to Incidents
Security as a bottleneck
Fragmented Tools
Budget Strain
Missed Vulnerabilities
After
Focused on what matters
Communicating business impact
Preventing breaches
Security as a business enabler
Unified platform
Comprehensive protection
Proven ROI
